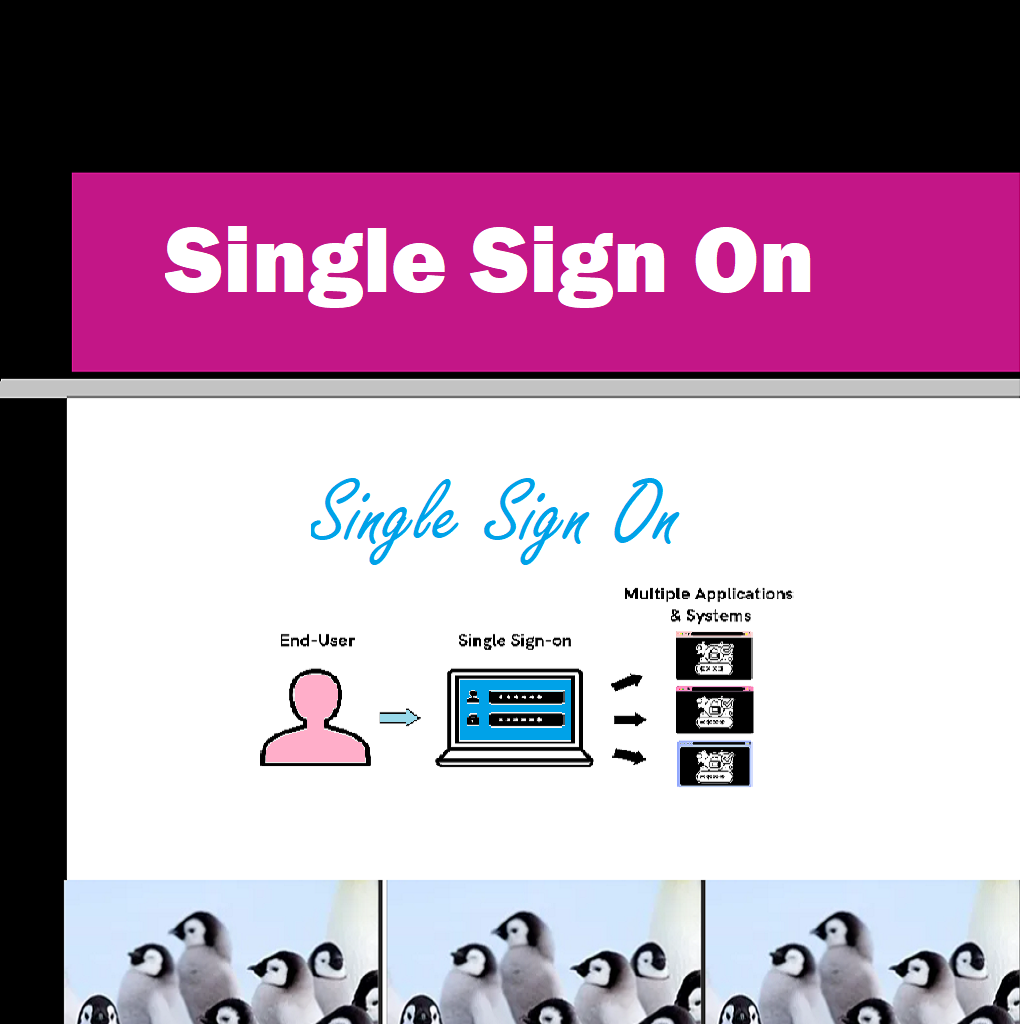
Single Sign On is an old concept now but still it is popular. Corporates across the globe use it for multiple reasons. Let’s go deep to find all about it. Single Sign-On (SSO) is an authentication mechanism that enables users to access multiple applications or systems with a single set of credentials. It is designed to simplify the login process and enhance security by reducing the need for multiple usernames and passwords. With SSO, users can log in once and gain access to various applications, services, or websites seamlessly.
The concept of SSO revolves around a central identity provider (IDP) that authenticates users and issues a token or a session identifier upon successful authentication. This token serves as proof of the user’s identity and is then presented to the various applications or systems the user wants to access. The applications or systems rely on the token issued by the IDP to validate the user’s authenticity and grant access.
One of the key advantages of SSO is improved user experience. Users no longer need to remember and manage multiple sets of login credentials for different applications. They can log in once and navigate between various resources without the hassle of repeated logins. This streamlines the user workflow, increases productivity, and reduces the frustration of dealing with multiple usernames and passwords. From a security perspective, SSO offers several benefits. Firstly, it reduces the risk of weak or reused passwords since users only need to remember a single set of credentials. This mitigates the common issue of password fatigue and encourages users to adopt stronger and more unique passwords. Additionally, SSO allows for centralized control and management of user access. Administrators can easily grant or revoke access to applications from a central location, ensuring consistent and efficient management of user privileges.
SSO implementations can vary, with different protocols and technologies used to establish trust and exchange authentication information between the IDP and the applications. Some commonly used SSO protocols include Security Assertion Markup Language (SAML), OpenID Connect, and OAuth. These protocols define the standards for exchanging authentication and authorization data securely.
In a nutshell, Single Sign-On (SSO) simplifies the authentication process for users by enabling them to access multiple applications or systems with a single set of credentials. It enhances security by reducing the reliance on weak or reused passwords and allows for centralized control over user access. SSO improves the user experience, increases productivity, and streamlines access management for administrators.
CONTENTS
High level technical visualization
Cost, time and effort required for implementation of SSO
Why SSO
SSO (Single Sign-On) offers several benefits and advantages, which explain why it is widely adopted and favored by organizations. Here are some key reasons why SSO is implemented:
- Improved User Experience: SSO simplifies the login process for users by eliminating the need to remember and manage multiple usernames and passwords for different applications. Users only need to authenticate once, and then they can seamlessly access multiple resources without the hassle of repeated logins. This convenience improves user experience, saves time, and reduces frustration.
- Enhanced Productivity: With SSO, users can quickly switch between applications and systems without the need for frequent logins. This streamlined workflow boosts productivity as users can focus on their tasks rather than dealing with authentication hurdles. It eliminates interruptions and allows for a more seamless navigation experience across various resources.
- Strengthened Security: SSO improves security in several ways. Firstly, it encourages the use of stronger and more unique passwords since users only need to remember a single set of credentials. This reduces the risk of weak or reused passwords that can be easily compromised. Additionally, SSO enables centralized control and management of user access. Administrators can enforce strong authentication policies, monitor user activity, and promptly revoke access when necessary, reducing the potential for unauthorized access and improving overall security posture.
- Centralized Access Management: SSO provides a centralized identity provider (IDP) that serves as the authentication authority. This centralization allows administrators to manage user access and privileges from a single location. They can easily grant or revoke access to applications, track user activity, and enforce security policies consistently across the organization. Centralized access management simplifies administrative tasks, reduces complexity, and ensures better control over user access.
- Integration and Compatibility: SSO protocols such as SAML, OpenID Connect, and OAuth are widely adopted and supported by a vast array of applications, platforms, and services. This compatibility allows organizations to implement SSO across a diverse range of systems, including cloud-based applications, on-premises software, and mobile applications. SSO enables seamless integration between different applications and simplifies the user experience across multiple platforms.
SSO is often implemented to enhance user experience, improve productivity, strengthen security, enable centralized access management, and ensure compatibility across various systems. It offers convenience for users, reduces administrative overhead, and contributes to a more secure and efficient authentication ecosystem within organizations.
Best way to implement SSO
The implementation of Single Sign-On (SSO) can vary depending on the specific needs and requirements of an organization. However, here are some general steps and best practices to consider when implementing SSO:
- Define Goals and Requirements: Begin by clearly identifying your organization’s goals and requirements for implementing SSO. Determine the systems and applications that need to be integrated, the desired user experience, and the level of security needed. This will help guide your implementation strategy.
- Choose an SSO Protocol: Select the appropriate SSO protocol based on your requirements and the compatibility of your applications. Common protocols include SAML, OpenID Connect, and OAuth. Each protocol has its own strengths and use cases, so evaluate them to find the best fit for your organization.
- Implement Identity Provider (IDP): Set up an Identity Provider, which will serve as the central authentication authority for your SSO implementation. The IDP will handle user authentication, generate and validate tokens, and manage user identities and access permissions. There are both commercial and open-source IDP solutions available, depending on your budget and preferences.
- Configure Applications for SSO: Integrate your applications with the chosen SSO protocol. This involves configuring the applications to trust the IDP and accept the authentication tokens issued by it. Most modern applications and frameworks provide built-in support for popular SSO protocols, simplifying the configuration process.
- Enable User Provisioning and Federation: Implement mechanisms to automate user provisioning and federation. User provisioning ensures that user accounts are created, updated, and deactivated automatically across the integrated applications based on the information stored in the IDP. Federation allows for the exchange of user identity information between different organizations’ IDPs, enabling seamless access across organizational boundaries.
- Test and Verify: Thoroughly test the SSO implementation to ensure it functions as intended. Test different user scenarios, application integrations, and security measures to identify and address any potential issues or vulnerabilities.
- Monitor and Maintain: Once SSO is implemented, establish a monitoring and maintenance plan. Regularly review logs and monitor user activity to detect any suspicious behavior. Keep the SSO infrastructure up to date with security patches and updates to mitigate vulnerabilities. Provide ongoing support and training to users and administrators.
- Educate Users: Conduct user awareness and training sessions to educate users about the benefits of SSO, how to use it effectively, and best practices for maintaining strong security.
It’s important to note that implementing SSO can be a complex process, and it may be beneficial to consult with experts or seek assistance from vendors who specialize in SSO solutions. They can provide guidance tailored to your organization’s specific needs and help ensure a smooth and secure implementation.
Popular SSO protocols
There are several SSO protocols commonly used in modern authentication systems. Here are some of the most widely adopted protocols:
- Security Assertion Markup Language (SAML): SAML is an XML-based protocol used for exchanging authentication and authorization data between an Identity Provider (IDP) and a Service Provider (SP). It enables web-based SSO and is widely used in enterprise environments. SAML uses assertions to communicate user authentication and attribute information.
- OpenID Connect (OIDC): OIDC is a protocol built on top of OAuth 2.0, designed for user authentication and identity information exchange. It provides an identity layer on OAuth 2.0, allowing clients (relying parties) to verify the user’s identity and obtain user profile information from an IDP. OIDC is widely used in modern web and mobile applications.
- OAuth 2.0: While OAuth 2.0 is primarily an authorization framework, it is also often used as an SSO protocol. OAuth 2.0 enables users to grant limited access to their protected resources (such as social media profiles or online storage) to third-party applications without sharing their credentials. It is commonly used in scenarios where applications require delegated access rather than full authentication.
- Microsoft Windows Integrated Authentication: This protocol is specific to Microsoft environments and allows for seamless SSO within the Windows ecosystem. It leverages the user’s Windows credentials and Active Directory to authenticate users and enable SSO across Windows-based applications and services.
- Kerberos: Kerberos is a network authentication protocol designed for secure authentication in a distributed environment. It uses symmetric key cryptography to authenticate clients and servers, allowing for SSO in Kerberos-enabled systems. Kerberos is commonly used in Windows domains and Unix-based environments.
- JSON Web Token (JWT): JWT is a compact and self-contained token format used for transmitting claims between parties in a secure manner. While not strictly an SSO protocol, JWTs are often used as tokens in SSO implementations to carry authentication and authorization information between the IDP and applications.
It’s essential to understand that different protocols have different features, levels of security, and use cases. The choice of protocol depends on factors such as the specific requirements of the application or system, interoperability needs, and the existing infrastructure and ecosystem. Organizations often select the protocol that best aligns with their security, compatibility, and usability goals.
SSO Technologies used
There are several SSO technologies and solutions available in the market that organizations can use to implement Single Sign-On (SSO). These technologies provide various features, functionalities, and deployment options. Here are some commonly used SSO technologies:
- Active Directory Federation Services (AD FS): AD FS is a Microsoft technology that enables organizations to establish trust relationships and provide SSO capabilities using the SAML or WS-Federation protocols. It integrates with Active Directory to authenticate users and share identity information with trusted applications or partners.
- Okta: Okta is a popular cloud-based Identity as a Service (IDaaS) platform that provides comprehensive identity management solutions, including SSO. It supports various SSO protocols such as SAML, OpenID Connect, and OAuth, and offers a wide range of features like multi-factor authentication, user provisioning, and centralized access management.
- Azure Active Directory (Azure AD): Azure AD is Microsoft’s cloud-based identity and access management service. It offers SSO capabilities and supports multiple SSO protocols like SAML, OpenID Connect, and WS-Federation. Azure AD provides a wide range of identity-related features and integrates well with Microsoft’s ecosystem, including Office 365 and Azure services.
- Ping Identity: Ping Identity provides identity and access management solutions, including SSO, for both on-premises and cloud environments. Their products support various SSO protocols like SAML, OAuth, and OpenID Connect. PingFederate is their flagship product that offers SSO capabilities along with other identity services.
- OneLogin: OneLogin is an IDaaS platform that offers SSO and identity management solutions. It supports SSO protocols like SAML, OAuth, and OpenID Connect and provides features such as multi-factor authentication, user provisioning, and centralized access control. It integrates with a wide range of applications and services.
- Salesforce Identity: Salesforce Identity is Salesforce’s cloud-based identity and access management solution. It provides SSO capabilities using industry-standard protocols like SAML and OpenID Connect. Salesforce Identity allows organizations to manage user identities, enforce security policies, and enable SSO for Salesforce applications and external resources.
- Shibboleth: Shibboleth is an open-source SSO framework that enables organizations to implement SAML-based SSO. It is widely used in higher education and research communities but can also be used in other sectors. Shibboleth provides identity federation capabilities and is highly customizable.
These are just a few examples of SSO technologies and solutions available in the market. The choice of technology depends on factors such as the organization’s requirements, budget, existing infrastructure, and integration needs. It is essential to evaluate different solutions and select the one that best fits the organization’s specific use case.
High level technical visualization
We can look at high-level technical outlining of a complete SSO implementation. Please note that the following description is a simplified representation and actual implementations may vary depending on the chosen SSO protocol and specific technologies used:
- User initiates the login process by accessing an application or service that supports SSO.
- The application redirects the user to the Identity Provider (IDP) for authentication.
- The user enters their credentials (username and password) on the IDP’s login page.
- The IDP verifies the user’s credentials against its user database or external authentication systems (such as LDAP or Active Directory).
- If the credentials are valid, the IDP generates an authentication token or session identifier.
- The IDP redirects the user back to the original application along with the authentication token.
- The application receives the authentication token and validates it by communicating with the IDP.
- The application verifies the token’s integrity, checks its expiration, and confirms its authenticity with the IDP.
- Once the token is validated, the application grants access to the user, who is now authenticated.
- The user can access additional applications or services that are integrated with the same SSO protocol without needing to re-enter credentials.
- When the user attempts to access another SSO-enabled application, steps 2-10 are repeated, but the user may not need to re-enter credentials if a session is still active or if single sign-on session persistence is enabled.
- The IDP manages user sessions, including enforcing session timeouts and handling session termination.
- Administrators can centrally manage user access, permissions, and policies through the IDP’s administration interface.
- The IDP can provide Single Logout functionality, allowing users to log out from all applications and terminate their session with a single action.
- The IDP may support additional features such as multi-factor authentication, password policies, and user provisioning for automated user account creation and management.
This textual representation provides a general overview of a complete SSO implementation, but the actual architecture and flow may vary depending on the chosen SSO protocol, the specific technologies used, and the integration requirements of the applications and systems involved.
Cost, time and effort required for implementation of SSO
The cost and time required to implement SSO (Single Sign-On) can vary significantly based on several factors, including the complexity of the environment, the chosen SSO protocol, the number of applications to integrate, the level of customization required, and the expertise and resources available within the organization. Here are some considerations:
- Infrastructure and Licensing Costs: The cost of implementing SSO can include infrastructure costs, such as hardware, virtual machines, or cloud resources, depending on whether the organization chooses an on-premises or cloud-based solution. Additionally, licensing fees may apply for commercial SSO solutions or IDaaS platforms.
- Integration Effort: The time and effort required for integration depend on the number and complexity of applications to be integrated with SSO. Applications may require customization or the development of connectors or adapters to support the chosen SSO protocol. Off-the-shelf applications with built-in SSO support can be easier to integrate.
- Deployment and Configuration: The time required to deploy and configure the SSO infrastructure depends on factors such as the complexity of the environment, the readiness of the existing infrastructure, and the expertise of the implementation team. Planning, installation, configuration, and testing can take anywhere from days to weeks or even months, depending on the scale and complexity of the implementation.
- Customization and User Provisioning: If customization or additional features are required, such as custom login pages, multi-factor authentication, or automated user provisioning, additional time and effort will be needed for development, testing, and deployment.
- Training and User Adoption: Consider the time and resources required to train users and administrators on the new SSO system. User adoption and acceptance may require education and support to ensure a smooth transition and minimize any potential disruptions.
It is challenging to provide specific cost and time estimates without a detailed understanding of the organization’s specific requirements and environment. Organizations are encouraged to engage with SSO solution providers or consultants who can assess the requirements, provide accurate estimates, and guide the implementation process. They can help determine the overall cost, timeline, and resource requirements for the SSO implementation project based on the specific needs of the organization.
Future of SSO mechanisms
The future of Single Sign-On (SSO) looks promising, as it continues to evolve and adapt to the changing landscape of technology and security. Here are some key trends and advancements that are shaping the future of SSO:
- Passwordless Authentication: Passwordless authentication methods, such as biometrics (fingerprint, facial recognition) and hardware tokens, are gaining traction. These methods provide a more convenient and secure alternative to traditional passwords, reducing the reliance on memorizing and managing complex passwords. SSO solutions are likely to incorporate and support passwordless authentication options for improved user experience and stronger security.
- Multi-Factor Authentication (MFA): MFA is becoming increasingly important in securing user access. SSO solutions are likely to integrate more seamlessly with MFA mechanisms, combining something the user knows (password), something the user has (smartphone, token), and/or something the user is (biometrics) for enhanced authentication security. MFA helps prevent unauthorized access even if credentials are compromised.
- Identity and Access Management (IAM) Convergence: The boundaries between SSO and broader IAM solutions are blurring. Organizations are looking for comprehensive IAM platforms that integrate SSO, user provisioning, access management, identity governance, and other identity-related functionalities. SSO solutions are evolving to offer more extensive IAM capabilities to provide a holistic approach to managing user identities and access across diverse applications and systems.
- API-Based SSO: With the increasing adoption of cloud services, microservices, and APIs, SSO is extending its capabilities to provide seamless authentication and authorization for APIs. API-based SSO allows secure access to web APIs, enabling developers to integrate applications more easily and securely. This trend aligns with the growing need for secure and efficient integration of diverse systems and services.
- Privacy and Consent Management: As data privacy regulations and user consent requirements become more stringent, SSO solutions will likely focus on privacy-enhancing features. This includes granular control over user data sharing, transparent consent management, and compliance with privacy regulations such as the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA).
- Federation and Interoperability: The demand for federated SSO is increasing, enabling users to access resources across different organizations and domains seamlessly. SSO solutions are evolving to support federated identity protocols and standards, facilitating secure identity federation and interoperability between organizations, cloud services, and external partners.
- User-Centric Experiences: SSO solutions are placing more emphasis on user-centric experiences, focusing on ease of use, personalization, and customization. Features like social login, self-service password reset, and contextual authentication are being integrated to provide a frictionless and personalized user journey.
The future of SSO is geared towards enhancing security, improving user experience, and providing comprehensive identity management capabilities. SSO solutions will continue to adapt to emerging technologies and security challenges to meet the evolving needs of organizations and users in an increasingly interconnected digital world.




You’ve the most impressive websites.
Thank you for sharing your thoughts. I really appreciate your efforts
and I will be waiting for your further write
ups thanks once again. https://Evolution.Org.ua/